Multi-Factor Authentication (MFA)

YouTube
Just in Time Permissions Explained #Delinea #PAM #CyberSecurity
Navigating NY DFS Regulation for PAM and MFA
Understanding the NY DFS Regulation for PAM and MFA
As IT professionals, it’s essential to keep up with evolving regulations, especially regarding data security like the NY DFS Regulation for PAM and MFA. This regulation responds to increasing cybersecurity threats faced by financial institutions in New York, mandating robust PAM and MFA controls.
Compliance with regulations is crucial in today’s digital landscape, especially for IT professionals. This subchapter focuses on the NY DFS Regulation for PAM and MFA, providing IT experts with the tools to navigate this complex regulatory environment.
Compliance with NY DFS regulations is vital for IT professionals in the financial sector. These regulations aim to enhance security and protect sensitive customer data, allowing IT professionals to safeguard their organization’s reputation and maintain customer trust.
Non-compliance with NY DFS regulations carries severe consequences, including fines and reputational damage. IT professionals must thoroughly understand regulatory requirements and conduct audits to identify compliance gaps and implement corrective measures.
Understanding Privileged Access Management (PAM)
To comply with NY DFS Regulation, organizations must conduct regular audits of their PAM systems. This involves:
Privileged Access Management (PAM) is vital in modern cybersecurity frameworks, especially with NY DFS regulations. This subchapter guides IT professionals on PAM’s importance, its role in NY DFS Regulation for PAM and MFA, and steps for audits and assessments.
PAM encompasses policies, processes, and technologies to manage access to privileged accounts. These accounts have elevated permissions, posing risks if not managed properly, as they can be exploited for unauthorized access and compromise security. In NY DFS Regulation for PAM and MFA, PAM ensures compliance with cybersecurity requirements by mandating robust controls. It protects privileged accounts from unauthorized access through authentication, authorization, and monitoring mechanisms, reducing the risk of data breaches.
In today’s digital landscape, robust security measures are paramount due to the escalating cyber threats and regulatory actions.
The NY DFS Regulation for PAM and MFA stands out as one such stringent regulation aimed at safeguarding sensitive information. This subchapter specifically focuses on Multi Factor Authentication (MFA) and its pivotal role in aligning with NY DFS regulations.
Key Requirements for Privileged Access Management
In cybersecurity, privileged access management (PAM) is crucial for safeguarding sensitive data and systems. The NY DFS Regulation for PAM and MFA emphasizes the need for IT professionals to understand key compliance requirements.
This regulation aims to bolster security in the financial services sector by mandating robust measures. Organizations must fulfill several key requirements:
1. Risk Assessment and Analysis
2. Access Controls and Monitoring
3. Multi-Factor Authentication (MFA)
4. Privileged User Tracking and Reporting
5. Security Awareness Training
6. Incident Response and Recovery
Assessing MFA Solution Options
In the dynamic realm of technology and cybersecurity, IT professionals must stay updated on regulations like the NY DFS Regulation for PAM and MFA. Compliance ensures the safeguarding of sensitive data, necessitating a thorough assessment of MFA solutions.
NY DFS Regulation Mandates
The NY DFS Regulation mandates robust security measures, demanding IT professionals to select MFA solutions that align with its standards. These solutions should support multiple authentication factors and seamlessly integrate with existing systems, while offering centralized management capabilities.
Understanding the Audit and Assessment Process
Operating under NY DFS Regulation for PAM and MFA requires a thorough grasp of the audit and assessment procedures.
These processes act as crucial checkpoints, ensuring that privileged access management and multi-factor authentication systems align with the stringent security standards set by the New York Department of Financial Services.
During audits, NY DFS-approved third-party auditors meticulously evaluate an organization’s PAM and MFA systems, policies, and procedures. This scrutiny aims to assess effectiveness, resilience, and compliance, safeguarding sensitive data and financial systems against cyber threats.
Preparing for the Audit
Preparing for compliance with the NY DFS Regulation for PAM and MFA demands meticulous planning for the audit and assessment process.
Conduct a rigorous internal assessment to identify gaps or weaknesses in existing PAM and MFA protocols.
Integrating PAM with Existing IT Systems
Compliance with NY DFS regulations for PAM and MFA is vital for financial organizations.
Start by understanding the specific requirements outlined in the NY DFS regulations.


Best Practices for Maintaining NY DFS Compliance
In the realm of IT security, compliance with regulatory standards like the NY DFS Regulation for PAM and MFA is paramount.
In the dynamic field of cybersecurity, compliance with regulations like the NY DFS Regulation for PAM and MFA is essential. This regulation imposes strict security measures for financial institutions in New York, necessitating thorough understanding and regular audits for compliance.
In today’s evolving digital landscape, cybersecurity threats are growing in complexity, compelling organizations to fortify their defenses and meet stringent regulatory standards.
Case Studies of Successful NY DFS Compliance
Case Study 1: Company A's Approach to PAM and MFA Compliance
In this chapter, we explore how
Company A, a leading financial
institution, implemented a robust
Privileged Access Management
(PAM) and Multi-Factor
Authentication (MFA) strategy to
meet New York Department of
Financial Services (NY DFS)
regulations.
Case Study 2: Company B's Journey to Achieve NY DFS Compliance
1. Introduction
2. Background
3. Challenges Faced
4. Steps Taken
5. Audit and Assessment
6. Conclusion
Future Trends and Challenges in NY DFS Regulation for PAM and MFA
1. Emerging Technologies and their
Impact on Compliance
2. Anticipated Changes in NY DFS Regulation
3. Overcoming Challenges in
Maintaining Compliance
Conclusion
Key Takeaways for IT Professionals
As an IT professional, comprehending the New York Department of Financial
Services (NY DFS) regulations for Privileged Access Management (PAM) and
Multi-Factor Authentication (MFA) is essential, though it can be intimidating. This
subchapter focuses on highlighting the key takeaways from these regulations,
emphasizing their importance in maintaining compliance and safeguarding
sensitive data.
Final Thoughts and Recommendations
Importance of NY DFS Regulation Compliance:
Understanding the significance of complying with the NY DFS regulation is paramount. These
regulations are implemented to safeguard sensitive data and mitigate cyber threats, ensuring the
protection of your organization's reputation and client trust.
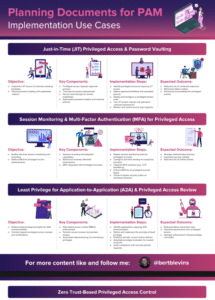
Just-in-Time (JIT) Privileged Access & Password Vaulting
- Objective:
- Key Components:
- Implementation Steps:
- Expected Outcome:
Session Monitoring & Multi-Factor Authentication (MFA) for Privileged Access
- Objective:
- Key Components:
- Implementation Steps:
- Expected Outcome:
Least Privilege for Application-to-Application (A2A) & Privileged Access Review
- Objective:
- Key Components:
- Implementation Steps:
- Expected Outcome:
Zero Trust-Based Privileged Access Control
- Objective:
- Key Components:
- Implementation Steps:
- Expected Outcome:
Automated Privileged Access Deprovisioning
- Objective:
- Key Components:
- Implementation Steps:
- Expected Outcome:
Privileged Access Risk Scoring & Anomaly Detection
- Objective:
- Key Components:
- Implementation Steps:
- Expected Outcome:
Cloud Privileged Access Management
- Objective: Secure privileged access in multi-cloud environments.
- Key Components: Cloud-native access controls
- Implementation Steps: Identify cloud-based privileged accounts and services.
- Expected Outcome: Consistent privileged access security across cloud platforms.

Endpoint Privileged Access Management (EPAM)
- Objective: Secure privileged access on endpoints (workstations, servers, etc.).
- Key Components: Local administrator rights management.
- Implementation Steps: Identify endpoints requiring privilege management.
- Expected Outcome: Reduced risk of endpoint privilege abuse.
CybersecurityPlan.ai
Building a Robust Cybersecurity Plan: The Power of Privileged Access Management (PAM) with Delinea
In today’s digital age, the cybersecurity landscape is evolving rapidly, with increasingly sophisticated threats targeting critical assets, sensitive data, and privileged accounts. Organizations face mounting challenges in protecting themselves from breaches, insider threats, and compliance violations. A well-structured cybersecurity plan is essential to safeguard business operations and maintain trust.
A cybersecurity plan is a comprehensive framework that outlines an organization’s strategies, policies, and controls to protect its digital infrastructure, data, and users from cyber threats. It includes risk assessment, threat detection, prevention measures, incident response, and continuous monitoring to ensure resilience against cyber attacks.
Privileged accounts—those with elevated permissions such as system administrators, network engineers, and application owners—are prime targets for cyber attackers. These accounts hold the keys to critical systems and data, making their protection paramount.
Privileged Access Management (PAM) is the cornerstone of an effective cybersecurity plan because it:
- Controls Access: Enforces least privilege by limiting privileged account permissions strictly to what is necessary
- Monitors Usage: Tracks all privileged session activity for auditability and anomaly detection.
- Secures Credentials: Safeguards privileged credentials using vaulting, rotation, and multi-factor authentication (MFA).
- Mitigates Risk: Reduces attack surfaces by minimizing opportunities for credential theft and misuse.
Delinea is a leading cybersecurity company specializing in Privileged Access Management. Their integrated platform provides a comprehensive suite of PAM capabilities tailored to protect identities, systems, and data across hybrid and multi-cloud environments.
Key Features of Delinea PAM:
- Credential Vaulting and Rotation: Secure storage and automated rotation of passwords and secrets to prevent unauthorized access.
- Session Management and Monitoring: Real-time monitoring and recording of privileged sessions for compliance and forensic analysis.
- Just-In-Time (JIT) Privileges: Dynamic, time-limited access to reduce standing privileged access risks.
- Least Privilege Enforcement: Granular control of privileges tailored to job roles and tasks.
- Least Privilege Enforcement: Enhanced authentication requirements for privileged access.
A successful cybersecurity plan incorporating PAM and Delinea involves these strategic steps:
1. Assess and Identify Privileged Accounts and Access
2. Define Access Policies and Roles
3. Deploy Delinea PAM Solutions
4. Monitor and Audit Privileged Access Activity
5. Continuously Improve and Adapt
- Expertise: Deep understanding of PAM and cybersecurity best practices.
- Customized Solutions: Tailored cybersecurity plans aligned with your business needs and compliance requirements.
- Latest Technologies: Guidance on leveraging advanced Delinea tools for maximum protection.
- Ongoing Support: Assistance in plan implementation, monitoring, and continuous improvement.
What is Multi-Factor Authentication (MFA)?
- Something You Know:
- Something You Have:
- Something You Are:
Why is MFA Essential in Today’s Cybersecurity Landscape?
- Preventing Account Takeovers:
- Mitigating Phishing Attacks:
- Protecting Sensitive Data:
Common Types of MFA Methods
- Authenticator Apps:
- SMS or Email Codes:
- Push Notifications:
- Hardware Tokens:
- Biometric Verification:
- Behavioral Biometrics:
Implementing MFA in Corporate Environments
- Compliance:
- Access Control:
- Remote Work Security:
- Integration with Privileged Access Management (PAM):
Best Practices for MFA Adoption
- Enforce MFA for All Users:
- Use Strong Authentication Factors:
- Regularly Update and Test MFA Systems:
- Educate Users:
- Monitor Authentication Attempts:
- Provide Backup Options:
The Future of MFA: Trends and Innovations
- Passwordless Authentication:
- Adaptive Authentication:
- Integration with AI and Machine Learning:
- Decentralized Identity Solutions:
About Bert Blevins and His Contributions to MFA Awareness
Resources & Learning
Step-by-step Guides: Learn how to enable MFA on popular platforms such as Google, Microsoft, Facebook, and financial institutions.
Video Tutorials: Access Bert Blevins’ easy setup guides and detailed explanations on OATH OTP, Just in Time Permissions, and Unlimited Admin Mode.
Industry News: Stay updated with the latest cybersecurity trends and MFA advancements through curated content and expert interviews.
Adding multi-factor authentication (MFA) to each of your accounts is a simple yet effective way to increase security. MFA alternatives are available from a wide range of online services, such as financial institutions, social media platforms, and email providers. In addition to your password, you’ll typically need to enter a code that you’ll get via SMS, email, or a specialized authenticator app when you enable MFA. Additionally, some systems allow biometric data or push notifications for the second criteria. Because the attacker would have to get beyond the other stages in order to access your accounts, this layered method ensures that your information is safe even in the event that one factor is compromised.
Beyond just enhancing personal security, MFA also safeguards confidential company data. Implementing MFA in a corporate setting helps protect consumer and intellectual property by preventing data breaches and illegal access to company systems.
The organization's overall security posture can be greatly improved by informing staff members on the significance of MFA and encouraging them to utilize it for all accounts linked to business. Adopting multi-factor authentication (MFA) as a routine security procedure is crucial for both individuals and enterprises to guarantee strong defense against prospective attacks, as cyber threats are always changing.
About Me

Bert Blevins is a distinguished technology entrepreneur and educator who brings together extensive technical expertise with strategic business acumen and dedicated community leadership. He holds an MBA from the University of Nevada Las Vegas and a Bachelor’s degree in Advertising from Western Kentucky University, credentials that reflect his unique ability to bridge the gap between technical innovation and business strategy.
As a Certified Cyber Insurance Specialist, Mr. Blevins has established himself as an authority in information architecture, with particular emphasis on collaboration, security, and private blockchain technologies. His comprehensive understanding of cybersecurity frameworks and risk management strategies has made him a valuable advisor to organizations navigating the complex landscape of digital transformation. His academic contributions include serving as an Adjunct Professor at both Western Kentucky University and the University of Phoenix, where he demonstrates his commitment to educational excellence and knowledge sharing. Through his teaching, he has helped shape the next generation of technology professionals, emphasizing practical applications alongside theoretical foundations.
YouTube
OATH OTP MFA Explained: Easy Setup Guide for Stronger Security
In his leadership capacity, Mr. Blevins served as President of the Houston SharePoint User Group, where he facilitated knowledge exchange among technology professionals and fostered a community of practice in enterprise collaboration solutions. He further extended his community impact through director positions with Rotary International Las Vegas and the American Heart Association’s Las Vegas Chapter, demonstrating his commitment to civic engagement and philanthropic leadership. His specialized knowledge in process optimization, data visualization, and information security has proven instrumental in helping organizations align their technological capabilities with business objectives, resulting in measurable improvements in operational efficiency and risk management.
Mr. Blevins is recognized for his innovative solutions to complex operational challenges, particularly in the realm of enterprise architecture and systems integration. His consulting practice focuses on workplace automation and digital transformation, guiding organizations in the implementation of cutting-edge technologies while maintaining robust security protocols. He has successfully led numerous large-scale digital transformation initiatives, helping organizations modernize their technology infrastructure while ensuring business continuity and regulatory compliance. His expertise extends to emerging technologies such as artificial intelligence and machine learning, where he helps organizations identify and implement practical applications that drive business value.
As a thought leader in the technology sector, Mr. Blevins regularly contributes to industry conferences and professional forums, sharing insights on topics ranging from cybersecurity best practices to the future of workplace automation. His approach combines strategic vision with practical implementation, helping organizations navigate the complexities of digital transformation while maintaining focus on their core business objectives. His work in information security has been particularly noteworthy, as he has helped numerous organizations develop and implement comprehensive security frameworks that address both technical and human factors.
Beyond his professional pursuits, Mr. Blevins is an accomplished endurance athlete who has participated in Ironman Triathlons and marathons, demonstrating the same dedication and disciplined approach that characterizes his professional work. He maintains an active interest in emerging technologies, including drone operations and virtual reality applications, reflecting his commitment to staying at the forefront of technological advancement. His personal interests in endurance sports and cutting-edge technology complement his professional expertise, illustrating his belief in continuous improvement and the pursuit of excellence in all endeavors.